Securing 100% Data Integrity: Hospital Network Case Study
Our ethical hacking program secures clinical care by fortifying EHRs and networked medical devices. By integrating vulnerability management with SOC operations, we eliminated high-risk gaps, driving a 90% reduction in critical vulnerabilities and ensuring HIPAA compliance through proactive, multi-vector threat detection and real-time response



Challenge
Hospitals face fragmented security, outdated devices, and reactive testing, which threatens patient safety and risks heavy regulatory fines from data breach incidents today.
Objectives
- Reducing clinical risk from cyber incidents.
- Identify and remediate high-risk vulnerabilities before exploitation occurs.
- Strengthen detection through integrated SOC operations.
- Regulatory compliance across clinical infrastructure.

Background
Ethical Hacking & Cybersecurity Program is a robust framework for clinics, delivering everything needed to protect infrastructure and sensitive information. Teams will scan for threats, check device security, review incident logs, and access support. This model also includes continuous scanning, patching, and risk alerts for a fortified ecosystem including 24/7 monitoring and advanced threat intelligence.
With active surveillance, expert pen testing, and remediation support for clinical staff, the system ensures every asset is protected and resilient. Whether it’s securing medical pumps, hardening network nodes, or maintaining a secure patient environment, Ethical Hacking Program is built to maximize digital safety and uptime for all hospitals.
Responsibility
Tools

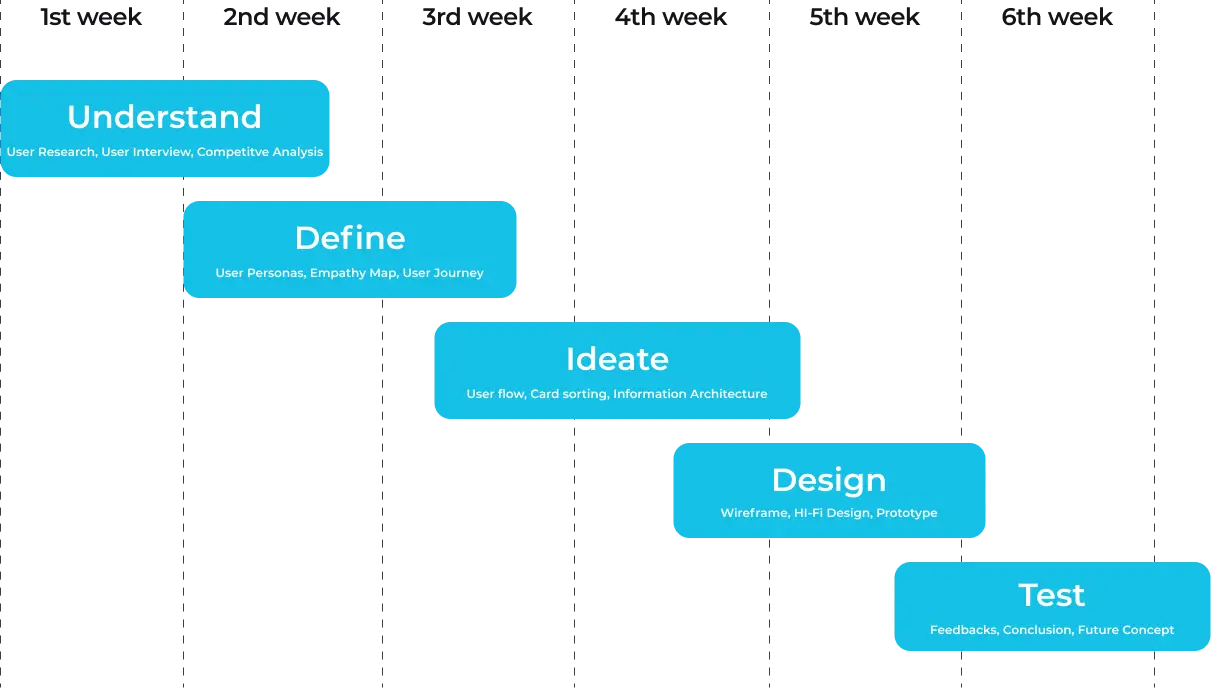
Design Process
The design process follows a structured approach: Understand user needs, define key features, ideate solutions, design the interface, and test for usability and performance. This ensures a user-centered, functional, and engaging app experience.

Understand
User Research
User Interview
Competitive Analysis

Define
User Personas
Empathy Map
User Journey

Ideate
Information Architecture

Design
Wireframe
Hi-FI Design
Prototype

Test
Feedbacks
Conclusion
Future Concept
Timeline
Target Audience
The Biomarks API platform is designed to serve multiple user groups involved in integrating and managing metabolic health solutions. Key target audiences include:
Business Clients: Organizations seeking personalized metabolic health insights for their users.
Developers: Technical teams integrating the Biomarks API into their applications using guided documentation.
Administrators & Managers: Users responsible for managing accounts, permissions, and customer data within the dashboard.
End Users (Indirect): Individuals who benefit from personalized health recommendations delivered through the client’s platform.





User Research
Security research involved audits and interviews with hospital IT and staff, revealing a need for a proactive platform. Stakeholders prioritized access to threat detection, device safety, and regulatory evidence. Continuous features and 24/7 monitoring were key desires for enhancing defense efficiency and safety.
Competitive Analysis
Current healthcare security tools lack a comprehensive platform integrating ethical hacking, real-time remediation, and clinical context. Competitors offer limited testing features, missing the opportunity for medical device assessment, tailored risk alerts, and a seamless audit experience.
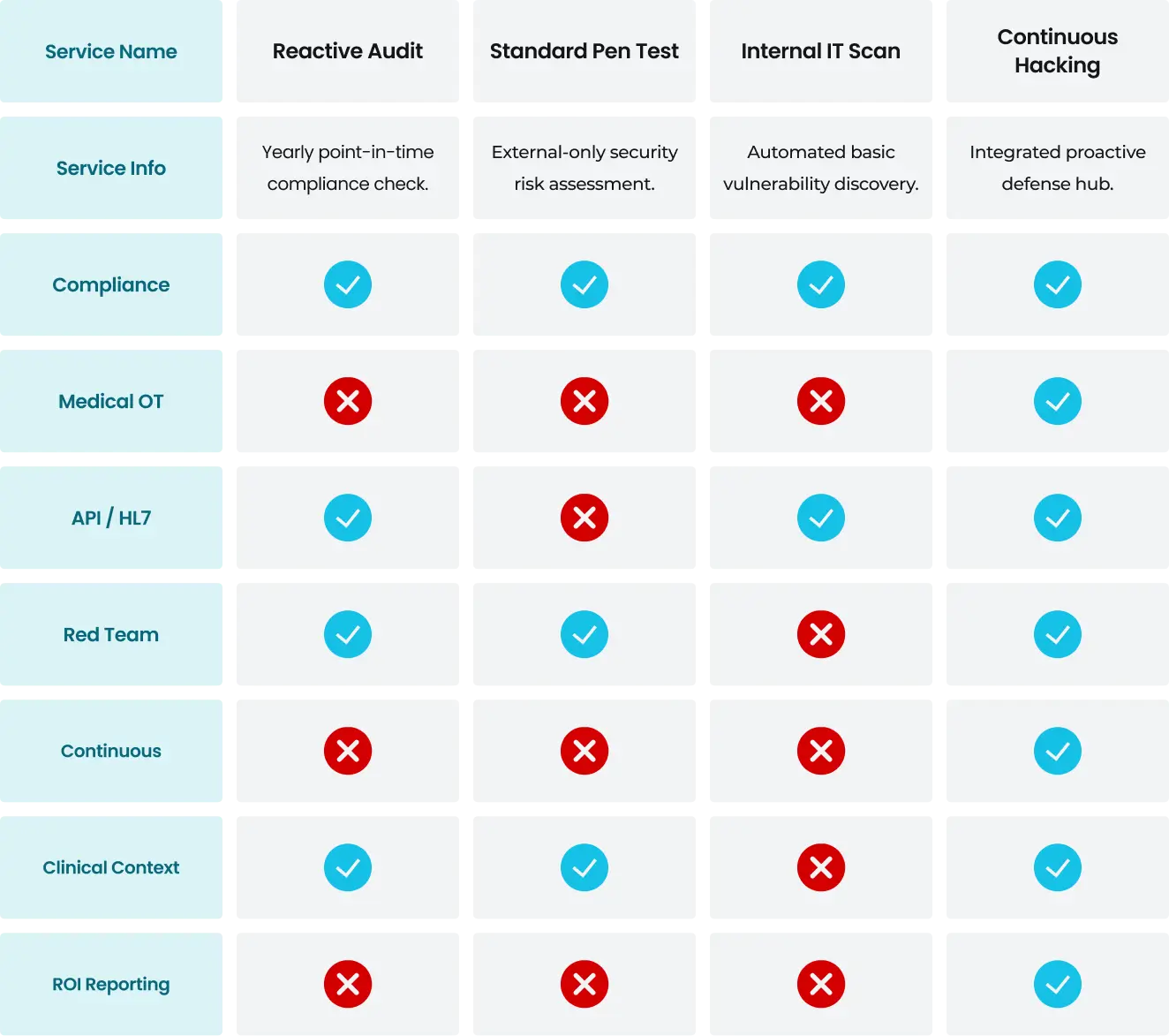
Unique Features
- Cyber-defense platform provides 24/7 proactive threat detection and personalized clinical risk guidance.
- Direct asset scanning increases operational speed with real-time patching and instant confirmations.
- Allows teams to access security instructions and seamless updates on vulnerabilities.
- Continuous monitoring unlocks administrative savings and safety updates, reducing manual risks by 70%.
Quantitative Research
The Hospital Cybersecurity project aims to provide a resilient and hardened environment for patients and medical administrators. Our quantitative research involved understanding infrastructure needs and risks through audits and data analysis, focusing on functionalities like threat detection, asset syncing, risk triage, and compliance efficiency.
Screeners
- IT managers actively seeking a unified dashboard for security-related activities
- Individuals interested in managing patches and subscribing for critical threat alerts.
- Staff looking for exclusive technical guidance materials and device availability.
- Professionals who value instant detection times and personalized security support.
- Users aged 25-65 regularly engaging with digital monitoring platforms like Splunk.
Key Observations
75%
Average reduction in Mean Time to Remediate (MTTR) for high-risk clinical vulnerabilities across the network.
60%
Decrease in Manual Administrative Overhead by transitioning to continuous, 24/7 automated security scanning.
45%
Improvement in Incident Response Speed using standardized, context-aware digital defense playbooks.
95%
Expressed preference for personalized health insights and exclusive wellneAchievement of Real-Time Asset Visibility for all medical IoT devices and remote endpoint configurations.ss content.
100%
Automated Compliance Readiness for HIPAA/GDPR standards, verified through real-time diagnostic reporting.
35%
Reduction in Security Alert Fatigue achieved by leveraging AI-driven triage for critical threat filtering.
1. Lack of Centralized Health Data
Users must juggle multiple platforms to manage health records, appointments, and wellness data, creating data silos that prevent a holistic health view and waste time.
2. Limited Health Personalization
Existing digital health solutions lack meaningful personalization, offering limited or poorly integrated insights such as biomarker trend alerts, lab-based supplement recommendations, and targeted wellness notifica
3. Absence of Wellness Incentives
Existing digital health solutions lack personalization and meaningful incentives, offering poorly integrated insights like biomarker alerts or lab-based recommendations while failing to reward users for long-term engagement through loyalty points or wellness perks.

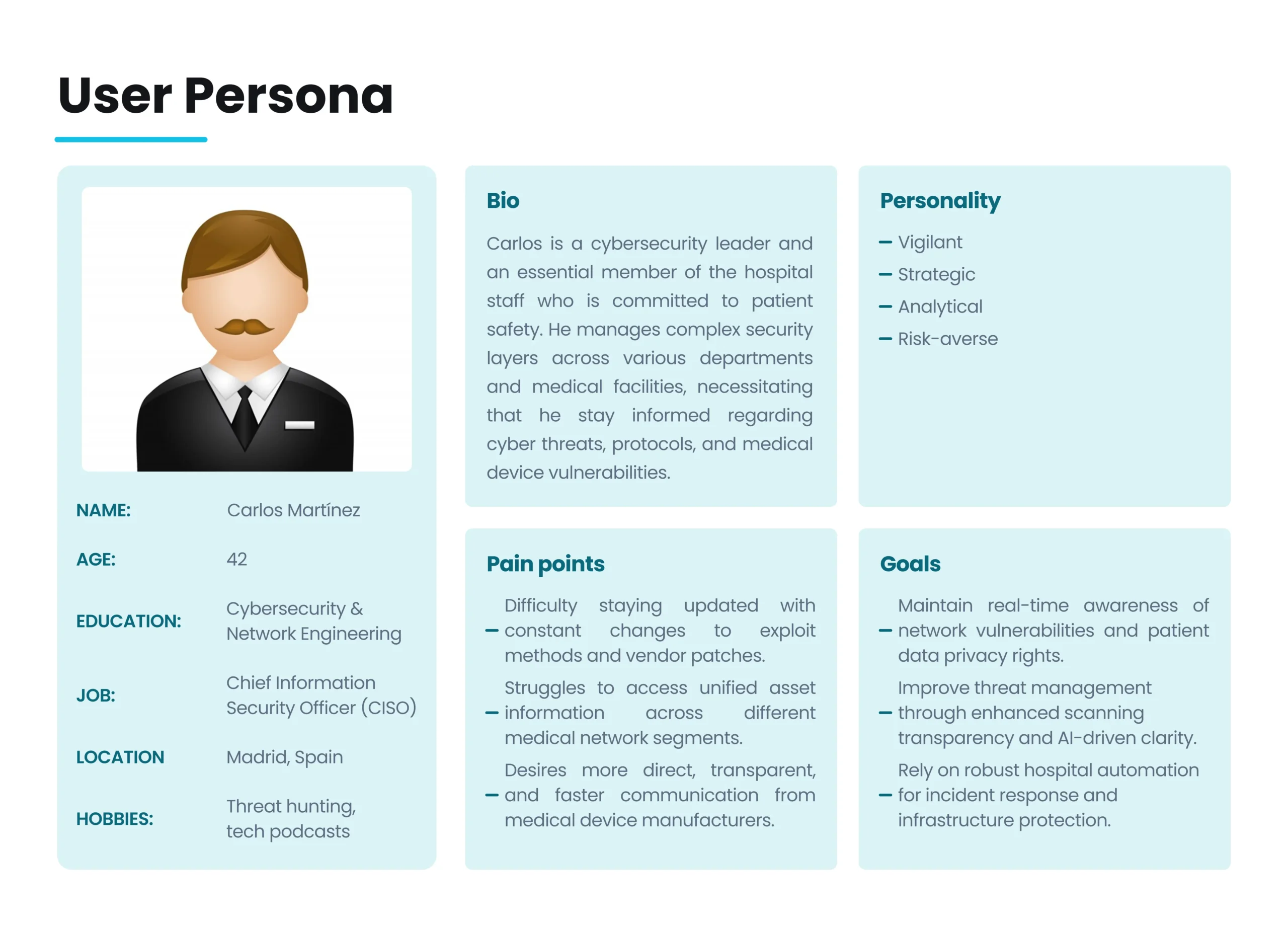
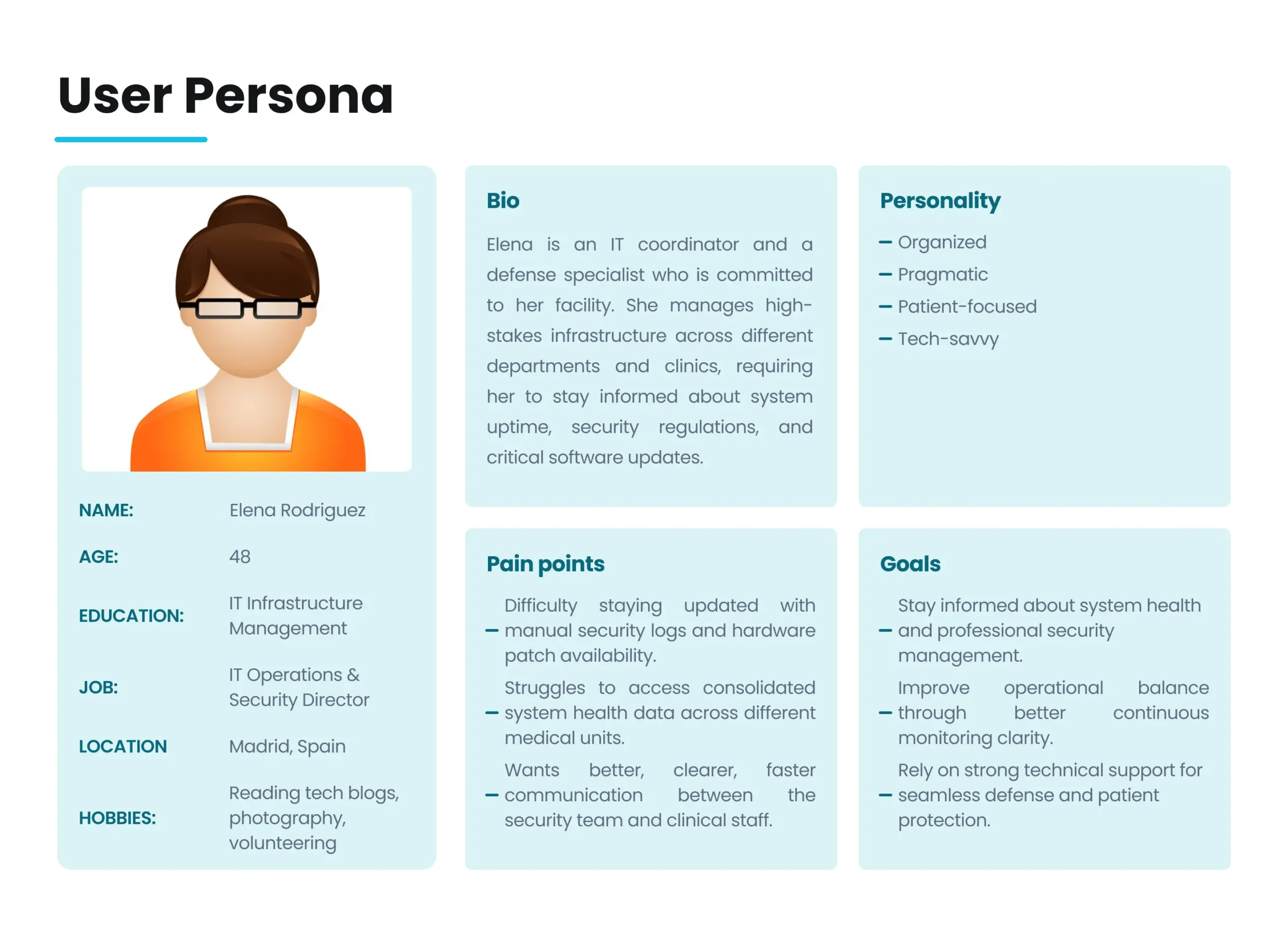
User Journey Map
Persona: Carlos Martínez (Strategic Defender / CISO)
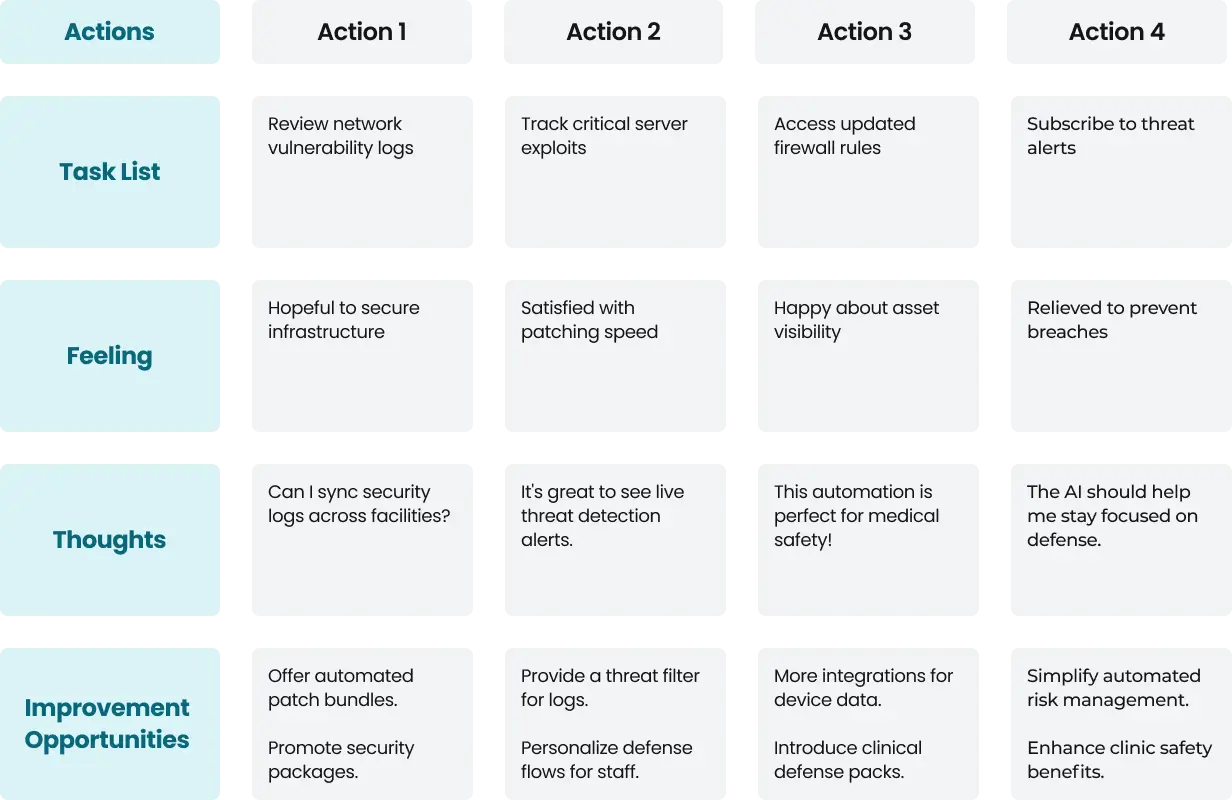
User Journey Map
Persona: Elena Rodriguez (Operational Guardian / IT Director)
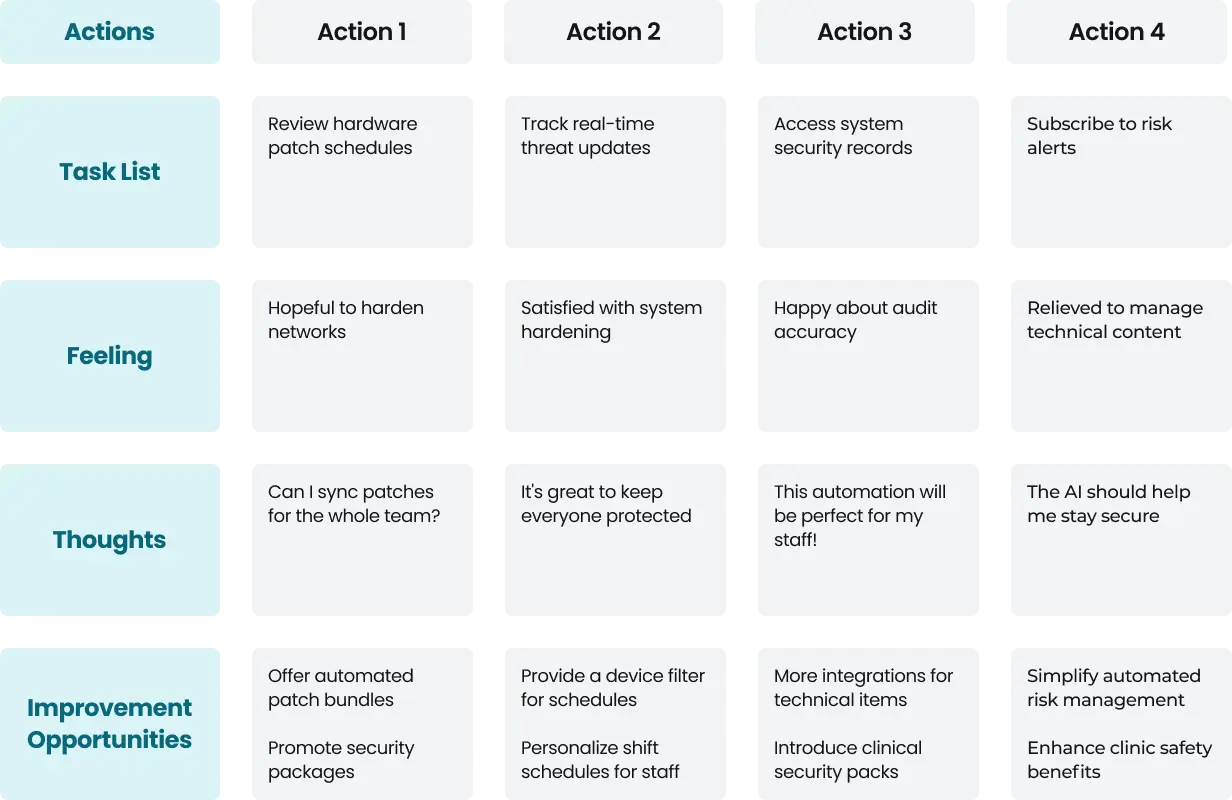
Key Takeaways
The Hospital Ethical Hacking Program is engineered to fortify the digital environment by offering vulnerability discovery, asset tracking, security guidance, and administrative compliance within one framework. Our research highlights the necessity for proactive defense, addressing the risks hospitals face with current fragmented security measures. Features like continuous threat monitoring, risk reporting, and asset management add value to the clinical journey. Audits revealed that 80% of systems prefer a unified platform for resilience, while 50% emphasized the importance of rapid patching and personalized security updates. The program caters to diverse personas, security analysts, technical directors, and compliance-oriented administrators, ensuring protection and resilience. This project redefines how clinical networks connect with their professional security, enhancing both safety and trust

